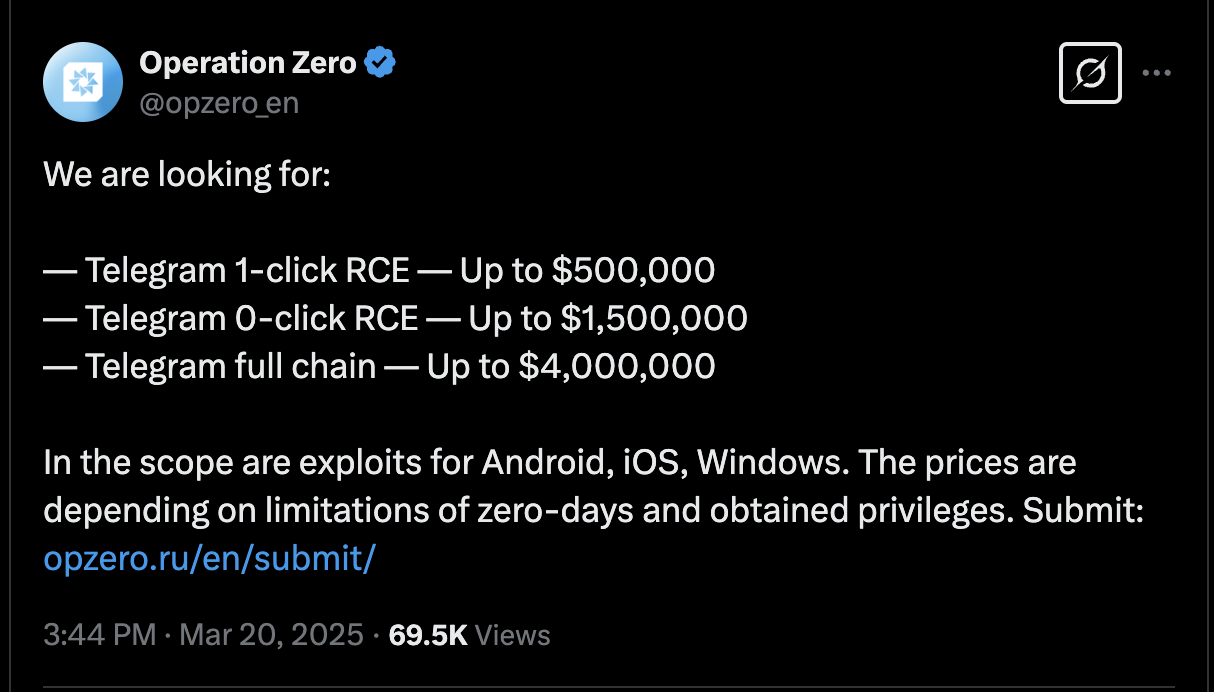
A Russian exploit brokerage firm, Operation Zero, has publicly announced bounties of up to $4 million for zero-day vulnerabilities in Telegram, signaling heightened state-sponsored interest in compromising the popular messaging app.
The company, which exclusively serves the Russian government and local entities, is seeking remote code execution (RCE) exploits across the Android, iOS, and Windows versions of Telegram. Payouts scale based on exploit sophistication.
Exploit Pricing and Targets
Operation Zero’s tiered pricing model includes:
| Exploit Type | Maximum Bounty |
|---|---|
| One-click RCE | $500,000 |
| Zero-click RCE | $1.5 million |
| Full-chain exploit | $4 million |
The “full-chain” category refers to multi-stage exploits granting access to a device’s operating system after the initial Telegram compromise.
 Claim on X
Claim on XIndustry sources suggest these prices may undercut market rates, as brokers often resell exploits to governments at 2–3x acquisition costs.
Telegram’s encryption and file-handling mechanisms have faced repeated scrutiny:
- Android: A July 2024 “EvilVideo” zero-day allowed attackers to disguise malicious APKs as videos, exploiting Telegram’s auto-download feature. Patched in version 10.14.5, the flaw required user interaction but highlighted risks in default settings.
- Windows: A 2024 typo-based vulnerability (mislabeling “.pyzw” files) enabled Python script execution, later mitigated by appending “.untrusted” to suspicious files.
- Historical Issues: Past flaws include a 2017 Unicode exploit enabling cryptomining malware delivery via disguised files.
Security experts note that Telegram’s encryption lags behind Signal and WhatsApp. Default chats lack end-to-end protection and use non-audited protocols.
These weaknesses, combined with its 1 billion+ user base, particularly in Russia and Ukraine, make it a high-value target for state-linked actors.
Operation Zero’s public bounty offers rare insight into Russia’s exploit procurement priorities. The move follows Ukraine’s 2024 ban on Telegram for government devices, citing infiltration risks from Russian hackers.
Industry analysts speculate the bounty reflects immediate demand from Russian agencies seeking surveillance or cyberwarfare capabilities.
While Operation Zero claims exclusivity to Russian clients, underground forums show broader exploit trade activity. The same “EvilVideo” vulnerability was advertised on Russian hacking forums in June 2024 before its patch, underscoring the blurred lines between state and criminal exploit markets.
Zero-day brokers like Operation Zero fuel a $12 billion global surveillance industry, with Telegram’s cross-platform dominance making it a perennial target. Users are urged to disable auto-downloads, enable encryption manually, and update apps regularly.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup – Try for Free
Content retrieved from: https://cybersecuritynews.com/russian-seller-telegram-0-day-exploits/.






